Access Control Profiles: Difference between revisions
No edit summary |
No edit summary |
||
| Line 1: | Line 1: | ||
'Tips for developers working within the Sysgem Enterprise Manager (SEM) environment'. | 'Tips for developers working within the Sysgem Enterprise Manager (SEM) environment'. | ||
---- | |||
''Access Control Profile settings grant or deny access to basic SEM features'' | ''Access Control Profile settings grant or deny access to basic SEM features'' | ||
'''Managing Access Control Profiles''' | |||
A SEM user account must have an Access Control Profile that is either inherited from a "Mirrored" SEM account or is directly allocated to this "Normal" SEM account. | A SEM user account must have an Access Control Profile that is either inherited from a "Mirrored" SEM account or is directly allocated to this "Normal" SEM account. | ||
Latest revision as of 09:24, 24 February 2011
'Tips for developers working within the Sysgem Enterprise Manager (SEM) environment'.
Access Control Profile settings grant or deny access to basic SEM features
Managing Access Control Profiles
A SEM user account must have an Access Control Profile that is either inherited from a "Mirrored" SEM account or is directly allocated to this "Normal" SEM account.
To manage Access Control Profiles use the SEM Menu option "Managers" > "SEM Users" > "Profiles" from a privileged SEM account (such as the System account).
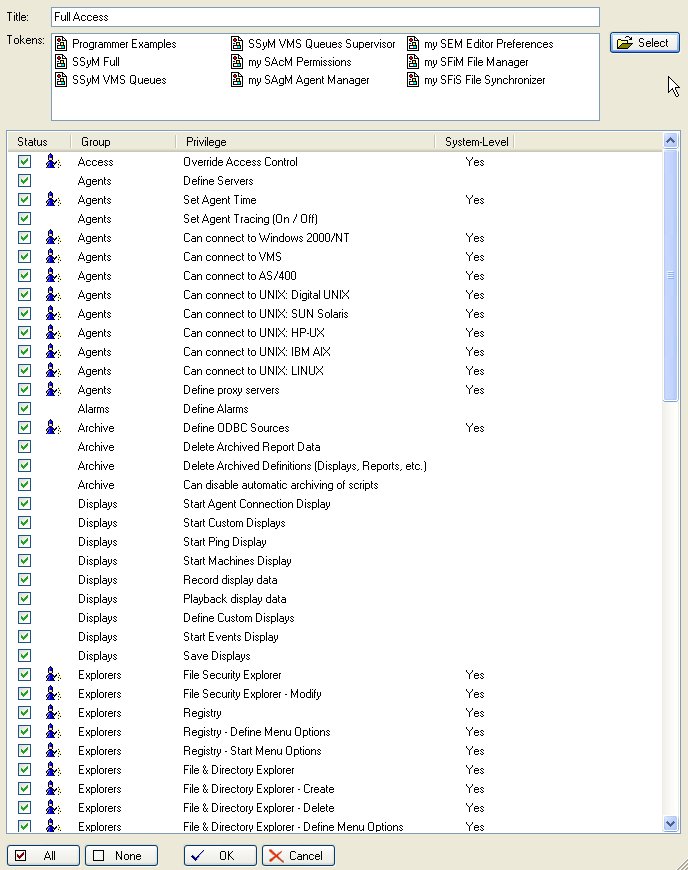
The following screen shot shows a section of the permission settings that are available in an Access Control Profile:
Note that the settings in a profile control access to basic SEM features. They do not control access to features within a SEM Module. To set access to the features in a SEM Module the "Access Control Token" needs to be managed for each particular SEM Module. After the settings have been applied to a Token, that token needs to be assigned to the "Profile" for the user by using the "Select" button at the top right of the Profile page (see above). In the example above there are nine different Access Control Tokens that have been allocated to this Profile.
For information on setting Access Control Tokens see: Access_Control_Tokens